Remediation of Credential Leaks: API Token and SMTP Credentials
If you have found your credentials (API token or SMTP username and password) have been leaked by either yourself or a third party, be sure to take the following actions. This tutorial will guide you through the steps necessary to remediate credential leaks and ensure the security of your accounts and data.
Revoke Existing Credentials
In order to prevent unauthorized access, you must revoke the leaked credentials as soon as possible. This process varies depending on the type of credential.
MailerSend API Token
- Log in to your MailerSend dashboard.
- Navigate to the “Settings” page on the left sidebar.
- Click on the "API Tokens" tab.
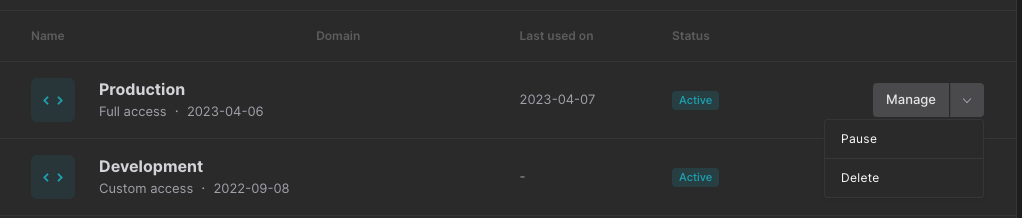
- Identify the leaked token, click the dropdown menu, and then the "Delete" button. This will immediately invalidate the token and prevent further access.
SMTP Username and Password
- Log in to your MailerSend dashboard.
- Navigate to "Domains" in the left sidebar.
- Select the affected domain name in the list.
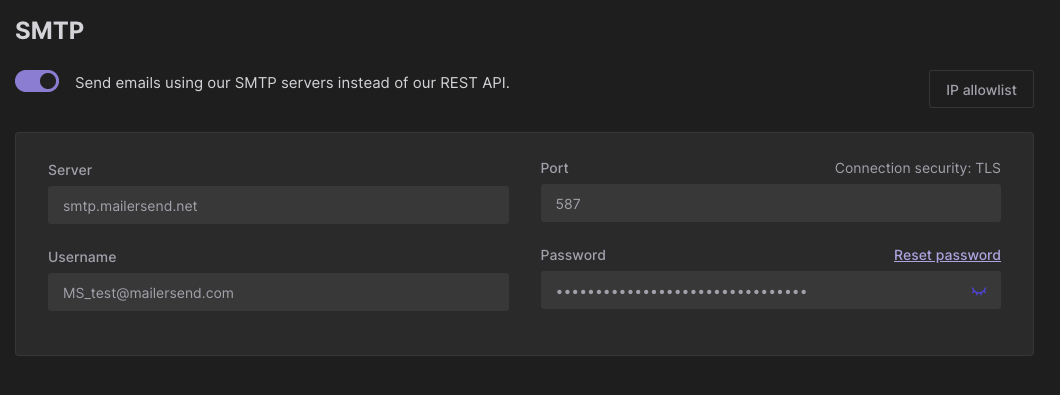
- Scroll down to the “SMTP” section and click the "Reset Password" button to create a new SMTP password. This will invalidate the old password and prevent unauthorized access using the leaked credentials.
Remove the Leaked Credential from Git Repositories (GitHub, GitLab, etc.)
Leaked credentials may remain in your repository's commit history even after being removed from your code's current version. To remove the leaked credentials from your Git history, follow these steps:
- Clone the repository locally if you haven't already.
- Use a tool like BFG Repo-Cleaner or git-filter-repo to remove sensitive data from your repository's history.
- Force-push the cleaned repository to overwrite the remote repository's history. Note that this may cause conflicts for other users, so communicate the changes to your team.
You may also just remove the credentials from your Git repo if doing a complete cleanup isn’t feasible.
Create New Credentials
After removing and revoking the leaked credentials, generate new ones to regain access to MailerSend services.
MailerSend API Token
- Return to the MailerSend dashboard and navigate to "Domains" in the left sidebar.
- Select your domain name in the list.
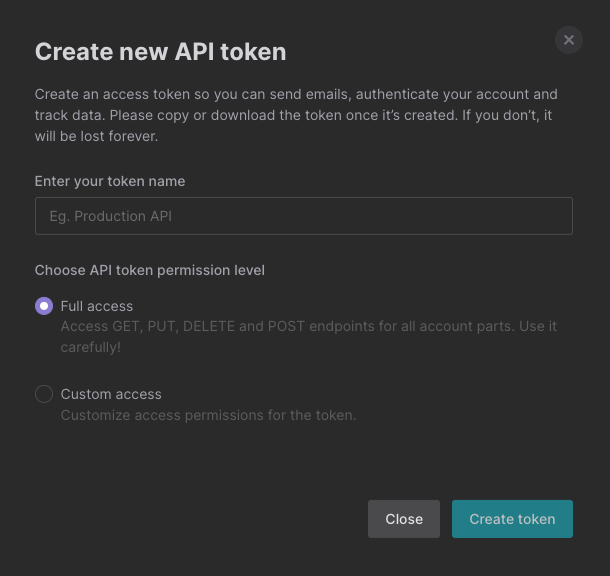
- Scroll to the "API Token" section and click the "Create new token" button.
- Assign a name to the new token and select the necessary permissions.
SMTP Username and Password
Use the new SMTP password you generated in the previous step. The SMTP username remains unchanged.
Securely Store and Use the New Credentials
To prevent future leaks, store and use your new credentials securely. Here are some best practices:
- Avoid hardcoding credentials in your source code
- Use environment variables to store sensitive information and access them in your code
- If you need to store credentials in a file, use a secure file format (such as .env) and add the file to your
.gitignoreto prevent it from being accidentally committed - Utilize a secret management service, such as HashiCorp Vault or AWS Secrets Manager, to securely store and manage sensitive information
- Educate your team about the importance of credential security and best practices
Following these steps, you can effectively remediate credential leaks and protect your MailerSend API tokens and SMTP credentials from unauthorized access.